Context-Enriched Metadata Reduces Your Teams’ Workloads
Patrick Bedwell, Head of Product Marketing
One of the features of Netography® Fusion that our customers value the most is the ability for them to add context to enrich the metadata analyzed by the Fusion platform. They have seen that metadata enriched with dozens of attributes from applications and services in their tech stack significantly reduces the workloads of their SecOps, NetOps, and CloudOps teams.
It’s great to know our customers value this feature so highly, because we think it’s essential for a security tool to reduce and not increase the demands on your teams. We understand the challenges they face:
- Trying to secure critical workloads distributed across cloud and on-prem environments
- Using too many siloed tools that rely on legacy technologies that aren’t effective today
- Spending too much time trying to understand the context of the low-fidelity alerts they’re flooded with
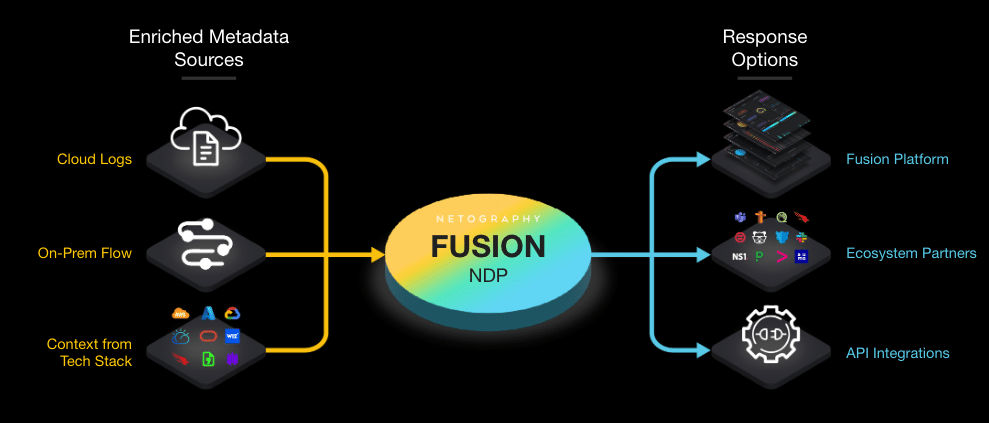
And that’s why we engineered Fusion––to help them secure their complex, dynamic, hybrid networking environments. Fusion is a cloud-native Network Defense Platform (NDP) that provides real-time detection and response to anomalies and threats across hybrid multi-cloud, and on-prem networks from a single console without deploying sensors or taps.
Enriching Metadata with Context
The Fusion platform starts with ingesting metadata from existing sources in your multi-cloud and on-prem networks:
- Flow data from the physical and virtual devices you have already deployed in your network, such as gateways, switches, and routers
- Cloud flow logs from Amazon Web Services, Microsoft Azure, Google Cloud, IBM Cloud, and Oracle Cloud
Fusion then enriches the metadata with context from 3rd party applications and services in your tech stack, including Active Directory, asset management, threat intelligence, configuration management databases (CMDBs) , endpoint detection and response (EDR), and vulnerability management (VM) systems.
The context can include dozens of attributes, including asset risk, type of entity, environment, last known user, region, and vulnerability counts, ratings, and scores. Fusion also normalizes the individual vendors’ naming conventions of each attribute to provide consistent attribute names across your diverse products and services.
Context Makes Your Analysts’ Lives Easier
Context-enriched metadata accelerates your teams’ investigations because your analysts don’t have to conduct additional research to understand the context of the activity, request access to different tools, or involve other teams. Fusion places the critical context at their fingertips to identify anomalous or malicious activity in real-time.
Your teams can quickly pinpoint suspicious or malicious activity immediately using Netography Detection Models (NDMs) to search billions of enriched and normalized records in seconds. They can customize the library of NDMs to monitor for anomalous activity in any combination of attributes, and across all network activity: North-South, East-West, on-prem to cloud, and cloud-to-cloud.
Here are some examples of how our customers use the enriched metadata in Fusion to accelerate and simplify their anomaly detection and response workflows:
- Compromise Detection and Threat Hunting: Fusion identifies anomalous activity and potential indicators of compromise in real-time in assets across your multi-cloud and on-prem network. The enriched metadata enables you to see potentially malicious activity targeting critical assets and workloads as it happens. You’ll be able to hunt for previously undetected IoCs and limit the scope of damage by responding in real-time, reducing the dwell time of any threat actors.
- Network Visibility and Analytics : Fusion monitors every conversation in real-time without deploying additional appliances across OT, IT, and IoT networks, including cloud, on-premises, and remote locations. Enriched metadata eliminates the need for you to use the “swivel chair” approach of relying on multiple tools and silos of data to research the potential significance of any activity.
- Governance: Many organizations lack the people, technology, or expertise to continuously monitor all activity in your network to ensure consistent, effective governance. Enriched metadata enables real-time alerting when it detects violations to Zero-Trust segmentation, PCI DSS or HIPAA data isolation, or social media policies.
- DDoS Efficacy and Attack Response Analytics: Fusion shows you the effectiveness of every element of your DDoS attack mitigation strategy. Enriched metadata enables you to see real-time analytics on your technologies’ ability to maintain availability of your authentication systems and customer-facing platforms. NDMs enable you to analyze critical pre- and post-scrub details on an attack, including source and destination attack traffic volumes.
- Vulnerability Management: Context from Wiz accelerates the detection of any current or past attempts to exploit unpatched vulnerabilities in your cloud assets. After being notified of a new vulnerability, you can immediately begin continuously monitoring all vulnerable systems for signs of targeting or compromise, until you have remediated the vulnerability. You can also analyze past activity related to vulnerable assets to identify potentially compromised assets.
Your analysts also have the flexibility to conduct their analysis, investigation, and response in the Fusion platform itself, or send the data to a SIEM or SOAR platform (or one of our other ecosystem partners) via Fusion’s built-in integrations or API, to match your existing workflows.
Fusion’s Enriched Metadata Improves Response Effectiveness
Recent Context Integrations in Fusion
Our engineering team adds context integrations in every release. Some recent context integrations include a wide range of technologies:
- Axonious, Device42, and runZero for asset management. Context attributes include architecture, cores, domain, interface name, kernel version, last user, domain, manufacturer, region, and subnet.
- Claroty for cyber-physical system security. Context attributes include asset ID, asset risk and criticality, MAC address, manufacturer, name, OS and version, serial number, and site.
- Microsoft Defender for endpoint security. Context attributes include architecture, MAC address, name, and OS and version.
Other recent integrations include Wiz for vulnerability management for cloud workloads and SentinelOne for endpoint security.

