Netography Fusion®
Real-Time Compromise Detection Across Clouds
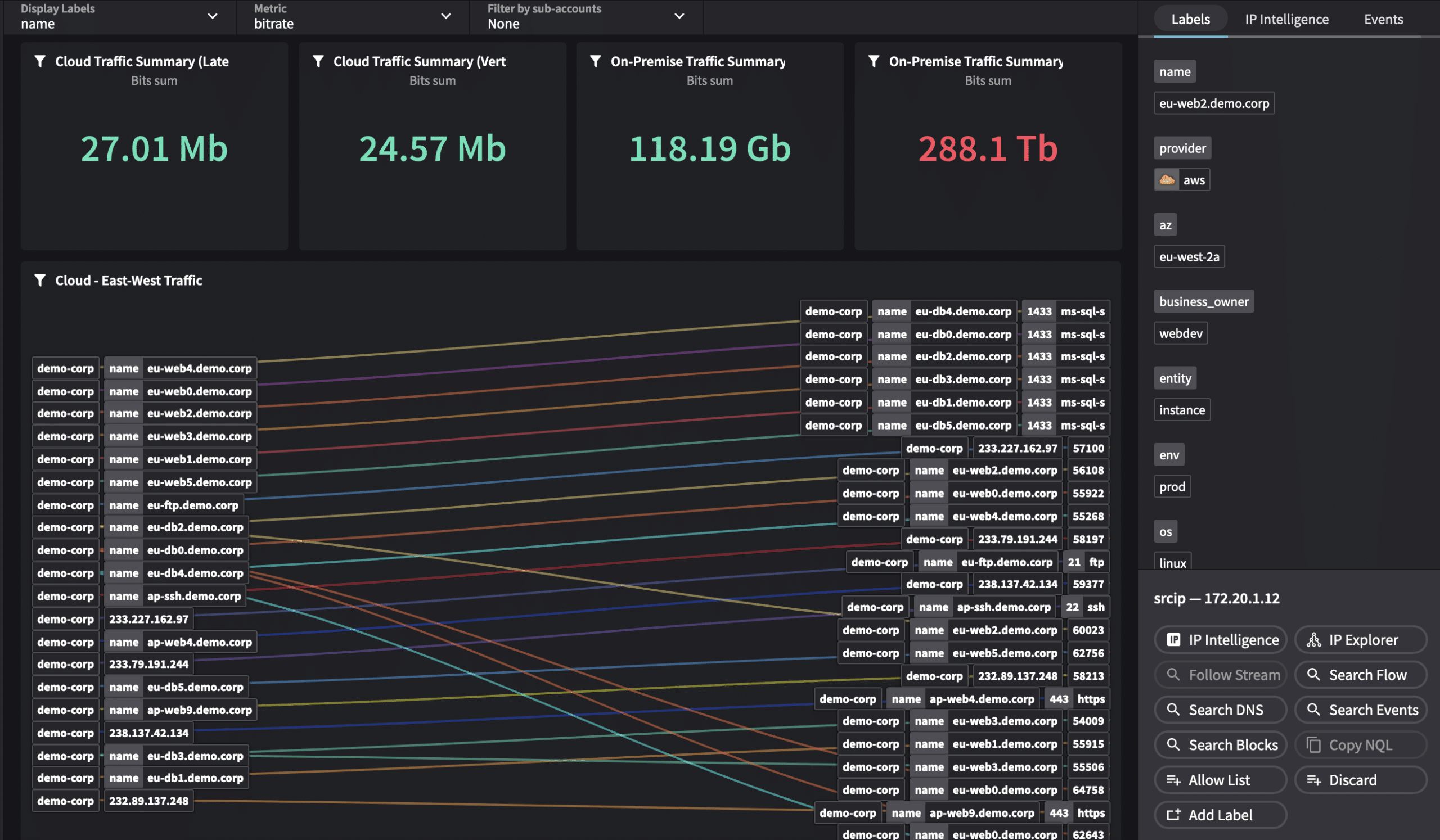
Netography Fusion detects activity that should never happen anywhere in your multi-cloud network, in real-time.
You’ll be able to visualize both East/West and North-South activity as soon as threat actors begin to move in your multi-cloud network, beacon to external systems, or engage in other anomalous activities consistent with a successful compromise.
You can respond before compromised cloud assets can cause costly operational disruptions or threaten business continuity.