Instant Access No Credit Card Required
The Fastest and Easiest Way to See All Network Activity
Fusion detects lateral movement and data exfiltration from ransomware in your multi-cloud or hybrid networks without the burden of sensors or agents.

"We achieved complete visibility and better security detections across all of our environments – including on-premises and multi-cloud, Netography Fusion ingests and enriches flow data at massive scale without hardware, complicated network taps in chokepoints, or costly deep packet inspection and decryption."
Shannon Ryan - FICO - Senior Director, Core Security Services and Architecture
How Fusion Works


Ingest
Orchestrate and normalize VPC and VNet flow logs, on-prem flow logs, and DNS logs from anywhere in your multi-cloud or hybrid network.
100% SaaS architecture eliminates the burden of deploying sensors, taps, probes, or agents.
Enrich
Enrich the flow and DNS logs with dozens of context attributes contained in your applications and services.
Context-enrichment transforms low-value IP address tables into context-rich descriptions of the activities of your users, applications, data, and devices.
Detect
Detect anomalous and malicious network activity with over 300 Netography Detection Models (NDMs).
You have complete flexibility to customize Fusion’s NDMs to deliver high-confidence, high-fidelity alerts to your CloudOps, NetOps, and SecOps teams.
Investigate
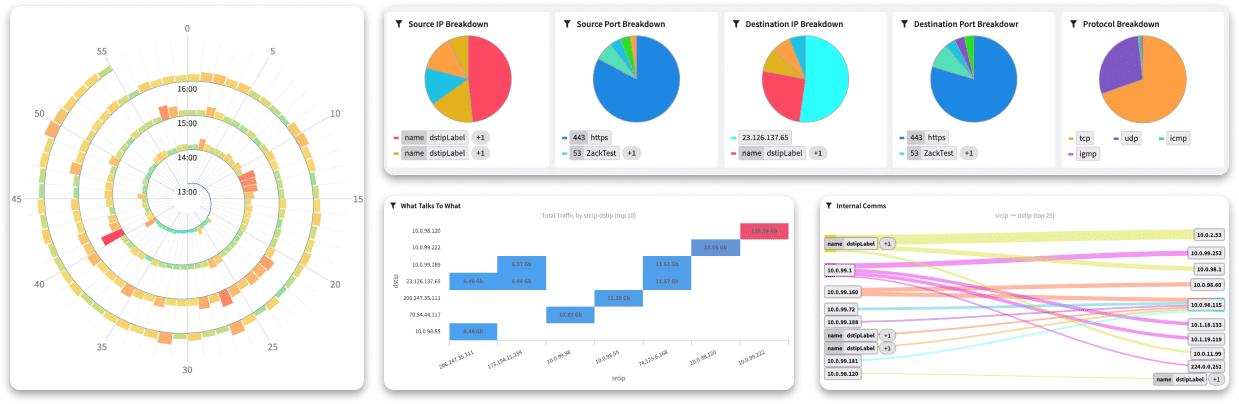
Conduct real-time and forensic analysis of the core evidence found in network activity logs to investigate anomalous or malicious activity.
Accelerate response time by utilizing up to 12 months of historical data to visualize changes in activity.
Respond
Execute response workflows quickly from within the Fusion SaaS platform or via built-in integrations with our technology partners.
You can also automate workflows using NetoFuse software that you can deploy within your own environment.
Detections
Detect anomalous and malicious activity with customizable Detection Models, including:
- Internal recon
Fusion automatically differentiates between your approved internal security scans and malicious activity- Example detection model: portscan
- Collecting and staging data
Fusion learns normal internal (east-west) network activity and identifies anomalous traffic patterns using machine learning.- Example detection: large_internal_smb_download
- Data exfiltration
Fusion learns normal outbound (north-south) network activity and identifies anomalous traffic patterns using machine learning.- Example detection: anomalous_traffic_s3,anomalous_traffic_dns, anomalous_traffic_ssh
- Anomalous lateral traffic from internal systems
- Botnet beaconing and C&C activity
- Communication with unusual assets/services
- Communication with embargoed nations
- Cryptomining
- Data harvesting & storage internally (pre-exfiltration)
- External access
- Post-compromise lateral movement
- Regulatory network segmentation violations (e.g., PCI DSS, GDPR, etc.)
- Social media usage
- Use of obfuscation technologies (e.g., Tor, VPN, DNS tunneling, etc.)
Integrations
Remove barriers caused by siloed data, teams, and tools, making your existing resources more effective.
Enrich Cloud Flow Logs and DNS Logs with Context
To address the lack of context in cloud flow logs and DNS logs, Fusion enriches that data with attributes from applications and services in your existing tech stack.
Fusion can associate dozens of context attributes with IP addresses, including:
- Asset risk
- Environment
- Last known user
- Region, risk score
- Security workgroup
- Type of entity
- Vulnerability count
Accelerate and Automate Response Workflows
The Fusion platform enables you to implement a range of response workflows in real-time. Respond from within the Fusion platform directly, or via built-in integrations with a range of technology partners:
- Push alerts to communication applications for distribution to diverse teams
- Send alerts to AIOps and IT management systems for automated remediation
- Forward alerts to SIEM and SOAR platforms for correlation with alerts from other security events to improve their detection fidelity
- Quarantine devices using integrations with EDR or XDR tools
- Block or redirect traffic from threat actors or reroute traffic for further analysis automatically using BGP, RTBH, Blocklist Manager, Flowspec over
- BGP, API and DNS orchestration.
5 Steps to Start Monitoring Your Network
Step 1
Add Cloud Flow Data Sources
Select the network traffic data you want to monitor:
- AWS VPC flow logs, AWS Transit Gateway flow logs
- Microsoft Azure NSG flow logs, Microsoft Azure VNet flow logs
- Google Cloud Platform (GCP) VPC flow logs
- Oracle Cloud (OCI) VCN flow logs
- IBM Cloud VPC flow logs
- NetFlow v5, NetFlow v9, NetFlow v10 (IPFIX) flow logs
- sFlow logs
Step 2
Add Context Integrations
Integrate context attributes from your tech stack to transform the value of your flow and DNS logs.
Fusion links dozens of context attributes like asset risk, environment, last known user, region, risk score, and vulnerability count to an IP address from almost any source, including:
- Cloud Providers
- Asset Management / Device Inventory
- Cloud Security
- Endpoint Protection (EPP)
- OT Security
- Vulnerability Management
Step 3
Add DNS Data Sources
Select the DNS data you want to monitor:
-
- AWS Route 53 request and response logs
- GCP Cloud DNS request and response logs
- Infoblox NIOS request and response logs

Step 4
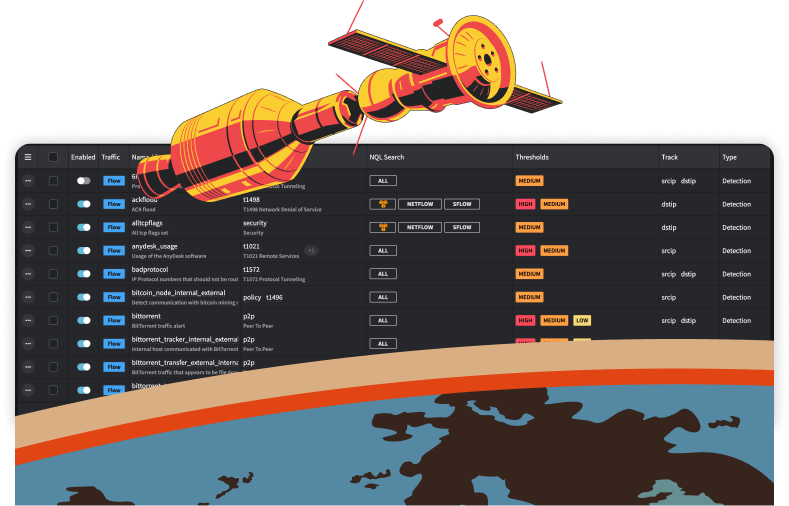
Enable Detection Models
Fusion includes over 300 customizable Netography Detection Models (NDMs) that you can enable to begin detecting malicious and anomalous network activity.
The NDMs categories are based on the MITRE ATT&CK® framework Tactics and Techniques, such as:
- T1537 Transfer Data to Cloud Account
- T1563 Remote Service Session Hijacking
- T1567 Exfiltration Over Web Service
Step 5
Add Response Integrations
Add response integrations with tools in your tech stack to automate response workflows when Fusion detects unwanted activity.
There are four types of response integrations offered by Fusion:
- Notification (e.g, Email, Slack, SIEM, Pagerduty, Webhook)
- Block (e.g., Blocklist, CrowdStrike, RTBH)
- DNS (e.g., repoint DNS queries to new IP address)
- Traffic (e.g, reroute traffic via BGP)