Ransomware Continues to Disrupt Operations
Ransomware has remained one of the most significant cybersecurity challenges organizations have faced for over a decade. Despite hundreds of millions of dollars invested in a range of technologies and end-user education, the impact of ransomware has continued to grow. In 2023, ransomware payments exceeded $1 billion for the first time.
Most Security Technologies Cannot Detect Ransomware
One of the primary reasons organizations continue to fall victim to ransomware is because much of the technology they have invested in simply cannot detect ransomware activity during any stage of an attack. There are several factors why existing technology isn’t able to keep up with the attackers, including:
- Distribution of critical data, applications, and systems across multiple cloud providers and legacy on-prem networks, as well as dissimilar IT, OT, and IoT operational environments.
- Deployment of a wide range of tools to monitor diverse environments, which creates silos of data that operations teams must stitch together to analyze.
- Continued reliance on detection technologies engineered initially for on-prem networks, which cannot operate at cloud scale nor within a shared responsibility model.
- Lack of ability to deploy agents on all workloads and systems in IT, OT, and IoT environments
- Cost of deploying sensors, taps, or probes to capture activity where agents are not deployed
- Boom in ransomware-as-a-service (RaaS) that put more sophisticated techniques within reach of unsophisticated cybercriminals
- Inability of many inspection-based tools (such as NGFW, NDR, or EPP) to block malicious content or links, thus not preventing initial compromise nor detecting post-compromise activity.
- Platform-native monitoring tools have a limited number of detections that identify any anomalous or malicious network activity (and are not ransomware-specific)
- Cloud-native tools like Cloud-Native Application Protection Platforms (CNAPP) and Cloud Access Security Brokers (CASB) do not monitor network-level activity and therefore do not see anomalous activity like lateral movement of a cloud asset.
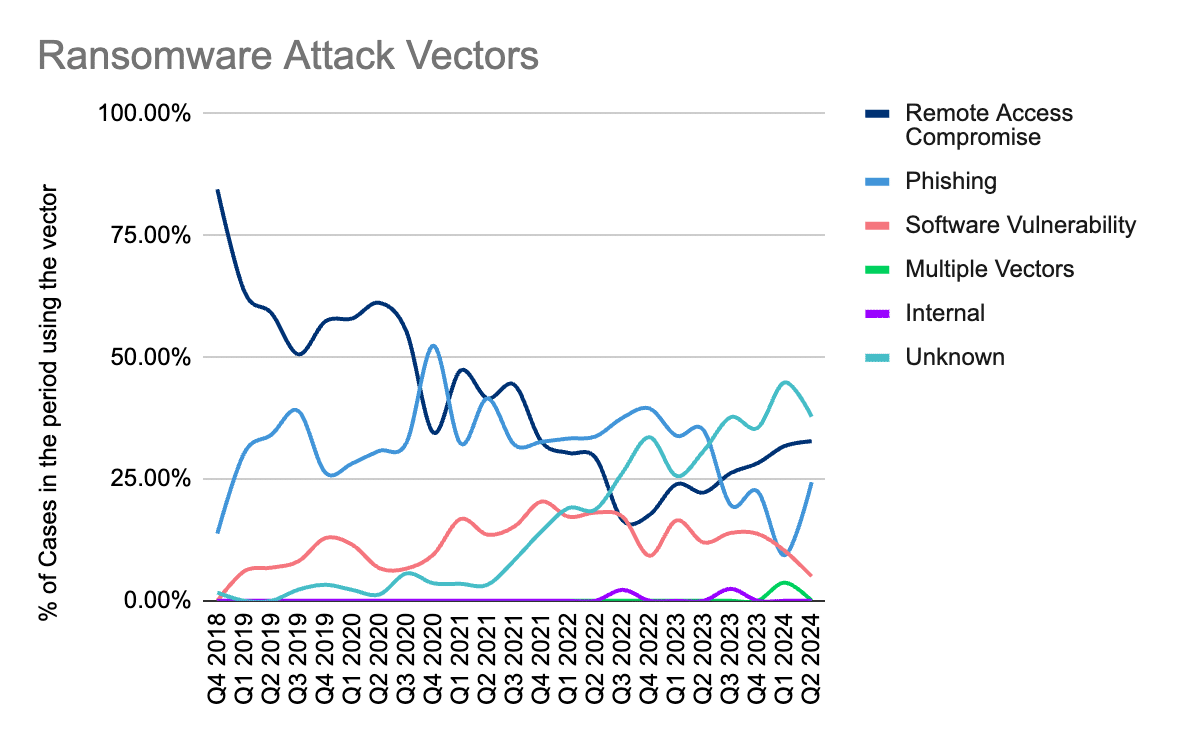
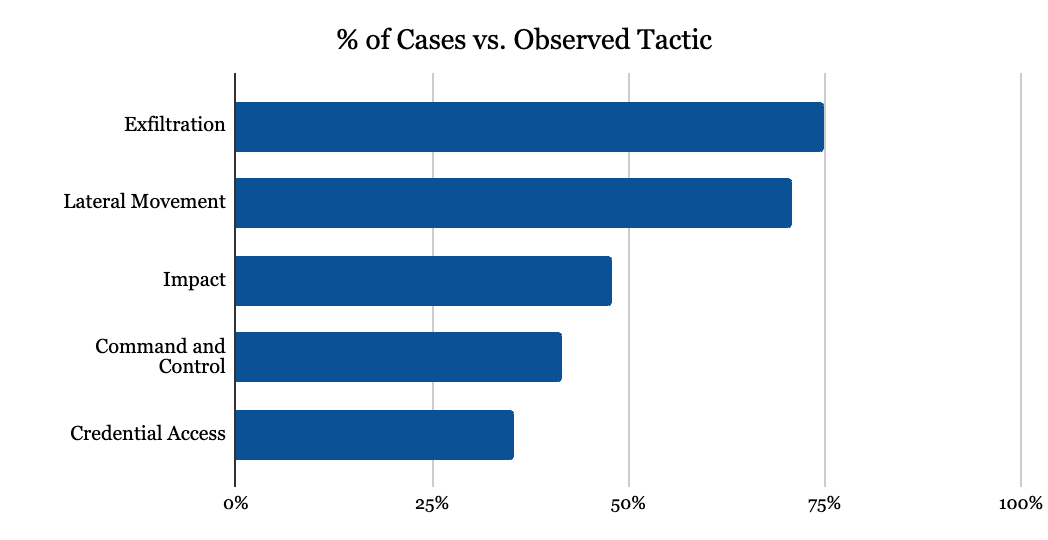
After a successful ransomware attack, operations teams lack the forensic data to identify the initial compromise vector. In Q2 2024.“Unknown” was the most common ransomware attack vector reported.