Implementing a Social Media Governance Control and Configuration Validation Program
By William Toll, Sr. Director, Product Marketing
Social media usage has become ubiquitous, and its usage by employees and organizations as a channel to communicate with their audience is widely considered extremely valuable. There has been some form of governance for social media for over 15 years. From the very first social media policies in the mid-2000s, including Microsoft’s famously simple “Be Smart” policy, to today’s comprehensive policies that HR, IT, and organization risk and compliance teams publish. A policy and the controls to enforce them has become vital. It is essential to implement monitoring, verification, and validation for adherence to these policies.
We’ve all read countless articles about employees, politicians, and celebrities who have been cited for crossing the line. For most organizations, there are notable risks for brand reputation damage, and employee and customer privacy. In addition, some organizations are in industries subject to regulations like the Deceptive Acts or Practices in Section 5 of the Federal Trade Commission Act and organizations that are subject to HIPAA violations. HIPAA governance includes abiding by the standards relating to permissible uses and disclosures of “Protected Health Information (PHI)”. This privacy rule effectively prohibits covered entities and business associates from using or disclosing PHI without an individual’s authorization.
And now, there are TikTok bans. Multiple government agencies and private businesses expressed concerns over the foreign ownership of the company, and its government’s access to private data. By April of 2023, TikTok is now banned for use on devices owned by the federal government. Also, in over 30 states, there are bans on its use by government agencies, employees, and contractors on government-issued devices. And more recently, some public universities are banning TikTok use on campus WiFi and university-owned computers.
Organizations have numerous solutions available to block or monitor social media usage – including browser plugins, endpoint content filtering software, and firewall configurations.
However, sophisticated users can bypass these controls, and disable endpoint controls and agents, or controls can be misconfigured or suffer from a lack of continuous updates that blocking social media access requires.
Netography Fusion’s operational governance capabilities ensure that the controls and methods in place are working or configured properly. This includes dashboards that break out social media network traffic – with context, enabling your analysts to see usage by social media networks. It’s easy to configure views by location, by device, and by employee role etc. We also support detections for unauthorized VPN use, which is often used by employees to bypass controls. Current usage detection for VPNs include NordVPN, Surfshark, ExpressVPN, CyberGhost, HMA, SoftEther, and Hotspot Shield.
Netography Fusion’s social media dashboards, when combined with custom Netography Detection Models (NDMs), include event alert configuration and response automation and are an incredibly powerful solution to ensure that your organization has the operational governance necessary to ensure that social media policies are being adhered to.
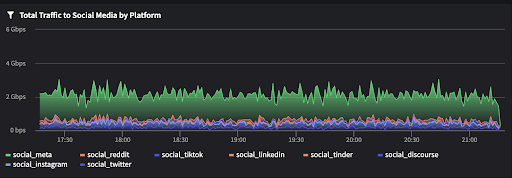
It’s easy to create custom dashboards for your existing social media policies. For example you can apply detections, alerts and responses for specific locations, departments, employee/contractor roles etc. The simple interface for creating dashboards, widgets, detection and alerts is shown here in the Dashboard Widget configuration panel.
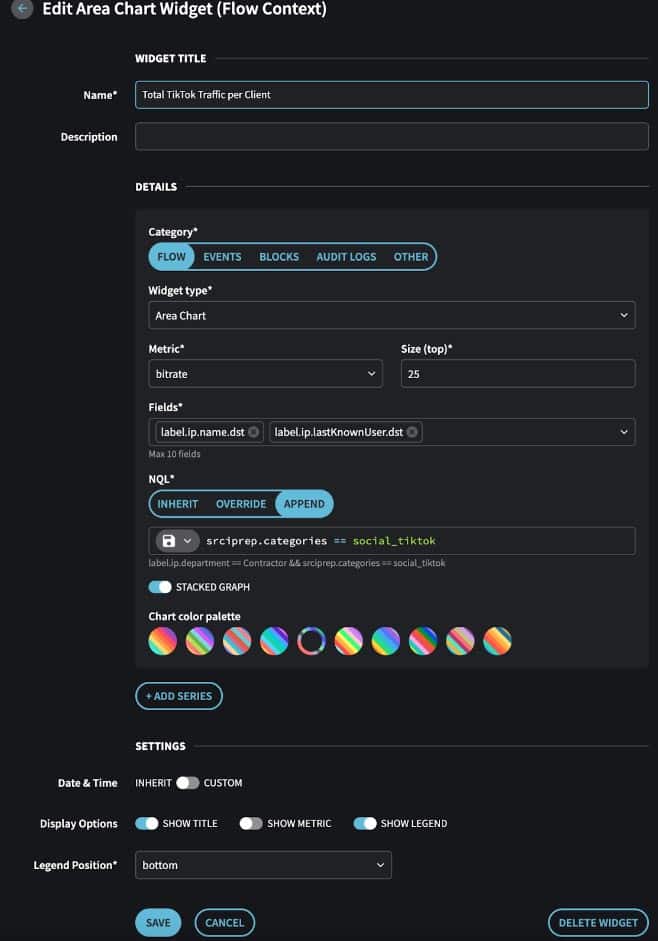
Netography Fusion Dashboard Widget Configuration Panel, including appending custom Netography Query Language (NQL)
With Netography Fusion’s Operational Governance capabilities, your teams are able to monitor and enforce security postures and policies in real-time and at scale. Netography Fusion enables organizations to greatly reduce cyber threat risks and ensure that organizational policies and changes to them can be rapidly enforced and monitored in real-time.