Accelerate Your Security Operations with Fusion’s MITRE ATT&CK Events View
by Patrick Bedwell
The Netography Fusion® platform maps detections from over 300 detection models to the MITRE ATT&CK framework, accelerating your response workflows to malicious activity.
Remind Me: What’s MITRE ATT&CK?
The non-profit MITRE Corporation created the MITRE ATT&CK framework over a decade ago to improve cyberattack detection and response. The framework organizes the tactics, techniques, and procedures (TTPs) threat actors use. It offers a structured and systematic approach for your security team to understand adversary behaviors and mitigate risk.
The framework categorizes threat actor actions into a matrix to describe both the tactics (the “why”) and the techniques (the “how”) of an attack:
- Each column lists a tactic a threat actor could use to achieve their objectives, such as Reconnaissance, Initial Access, or Lateral Movement.
- Each row represents a technique a threat actor could use to pursue a tactic, such as Active Scanning or Gather Victim Information as part of the Reconnaissance tactic.
Operationalizing the MITRE ATT&CK Framework with Netography Fusion
Netography Fusion gives you a holistic view of all network activity. It identifies malicious events anywhere in your multi-cloud or hybrid network in real-time and maps those events to the ATT&CK framework. Your operations team can initiate ATT&CK-informed playbooks faster and respond to malicious and anomalous activity more effectively.
Armed with context-rich, high-confidence alerts, your SecOps and NetOps teams can also conduct targeted investigations and threat hunting of specific TTPs while the attack is in progress, reducing the potential for operational disruptions.
- Investigation: Mapping observed behaviors to specific techniques and tactics helps your analysts identify the scope of the attack, understand how the adversary gained access, and what actions they may take next. For example, if Fusion detects that an attacker has exploited a public-facing application to gain initial access, ATT&CK helps identify the likely follow-up actions, such as Credential Access, Discovery, Lateral Movement, or Collection.
- Threat Hunting: ATT&CK empowers your hunters to systematically search for evidence of adversary behavior that might otherwise go undetected. For example, an attacker attempting to maintain Persistence in a system might use techniques like leveraging external-facing remote services to gain access to your network, which would cause Fusion to create an event.
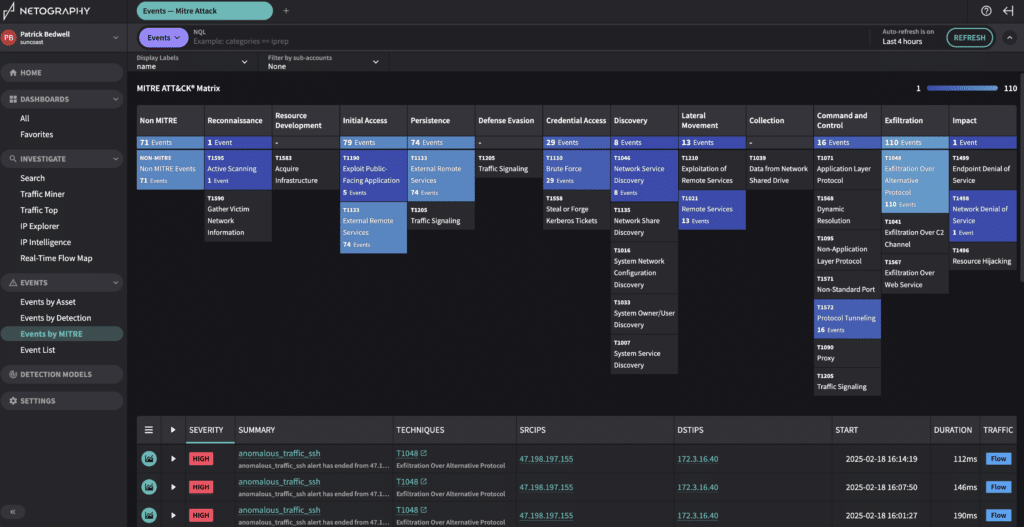
Fusion maps events to the MITRE ATT&CK framework for faster response
You can click any of the techniques listed on the heat map on the page to filter the event list by that technique.
Detect Malicious Activity Your Other Tools Miss
The Fusion platform is a cloud-agnostic, environment-agnostic, and encryption-agnostic alternative to outdated monitoring and detection technologies. Fusion’s 100% SaaS architecture eliminates the burden of deploying sensors, agents, taps, or probes.
Data Ingest
Fusion ingests network metadata from any part of your network where you want visibility:
-
- AWS VPC flow logs, AWS Transit Gateway flow logs
- IBM Cloud VPC flow logs
- Google Cloud Platform (GCP) VPC flow logs
- Microsoft Azure NSG flow logs, Microsoft Azure VNet flow logs
- Oracle Cloud Infrastructure (OCI) VCN flow logs
- NetFlow v5, NetFlow v9, NetFlow v10 (IPFIX) flow logs
- sFlow logs
Context Enrichment
Fusion enriches the metadata it ingests to transform IP address tables into context-rich descriptions of the activities of your users, applications, data, and devices. Fusion incorporates context already contained in your applications and services, including asset management, cloud-native application protection platforms (CNAPP), configuration management database (CMDB), endpoint protection agents (EPP), and vulnerability management.
Fusion can ingest dozens of attributes to enrich your metadata, including asset risk, environment, last known user, region, risk score, security workgroup, type of entity, and vulnerability count.
AI-Powered Detection
The Fusion platform detects anomalous and malicious network activity with over 300 open Netography Detection Models (NDMs). You have complete flexibility to customize Fusion’s NDMs to deliver high-confidence, high-fidelity alerts to your CloudOps, NetOps, and SecOps teams.
Fusion detects malicious activity before, during, and after a threat actor compromises your network, including:
-
- Pre-compromise reconnaissance (external-to-internal activity), such as brute force attacks and external use of internal services.
- Post-initial-compromise lateral movement (internal-to-internal activity) such as network scanning, brute force attacks, and ransomware staging over SMB.
- Post-compromise data exposure and exfiltration (internal-to-external activity) such as communication with known C&C/C2 infrastructure, anomalous data transfer over SSH and DNS, and data exfiltration to Amazon S3 buckets and private cloud storage services.
Investigate
Your operations and IR teams can conduct real-time and forensic analysis of the core evidence found in network activity logs to investigate anomalous or malicious activity.
Fusion’s capacity to retain up to 12 months of historical data will accelerate your teams’ ability to perform investigations by providing a complete picture of past network activity.
Respond
The Fusion platform enables you to implement a range of response workflows in real-time. Respond from within the Fusion platform directly or via built-in integrations with a range of technology partners:
-
- Push alerts to communication applications for distribution to diverse teams.
- Send alerts to AIOps and IT management systems for automated remediation.
- Forward alerts to SIEM and SOAR platforms for correlation with alerts from other security events to improve their detection fidelity.
- Quarantine devices using integrations with EDR or XDR tools.
- Block or redirect traffic from threat actors or reroute traffic for further analysis automatically using BGP, RTBH, Blocklist Manager, Flowspec over BGP, API, and DNS orchestration
We’re excited to show you how to leverage Netography Fusion to accelerate your ATT&CK-based workflows and bring more capability and value to your security operations.
Contact us for more information or see for yourself with a free trial.

