How Network Metadata and Netography’s Tools Empower Incident Investigations
by Netography Detection Engineering Team
Trend data from the M-Trends 2024 Special Report shows that global median dwell time (defined as the number of days an attacker is on a system from compromise to detection) has dropped significantly over the past decade, which is promising news. However, approximately 45% of intrusions still take weeks to months to detect, exposing organizations to significant risk.
The ability to investigate activities that have happened on your network in the past and reconstruct them is incredibly important when a security incident occurs. To ensure your security teams are prepared to handle the challenge, you need to ask:
Can we reasonably investigate with the tools that we have?
Can we search across enough of the data within the right timeframes so that we can reconstruct the origin and full scope of a security incident?
The Netography Fusion® platform accelerates detection and investigation of suspicious activity or potential signs of compromise on your network by using metadata from across your hybrid or multi-cloud environment.
In this blog, we’re going to focus on the value network metadata brings to investigations and some of the tools we give you to investigate what’s happening on your network when you learn of an incident.
Why network metadata is critical to investigations
There are three main reasons why bringing all your network metadata into Fusion is important:
- Resource efficiency. The network metadata that Fusion collects is a valuable resource for incident investigations because it provides important information about the behavior that hosts engage in on your network – what they are doing, what’s happening to them, and what normal activity looks like. Network metadata is also relatively inexpensive to store versus other types of network telemetry. So, you can affordably maintain more history with network metadata than you can with packet capture or other tools that you might be using to collect information.
- Centralized view. Organizations tell us they may be capturing firewall logs, but they aren’t collecting and maintaining a history of network metadata from other parts of their environment, especially their clouds. Fusion gives you one place where you can aggregate your metadata from your office environments, different cloud environments, and data centers. You have peace of mind that you can go to one place to see a complete record of everything that has happened on your network over several months.
- Comprehensive visibility. EDR tools provide useful data that teams often rely on for network investigations. But sometimes incidents span hosts that don’t have EDR installed – either they can’t support an agent, or you may not be aware of them, or they aren’t under your control. These include IoT and OT devices and cloud marketplace images. Incidents can also occur when a user uninstalls an EDR agent, perhaps to troubleshoot an issue, and neglects to reinstall it. There are many reasons why you may not have total coverage of your network with EDR and why it is useful to collect network telemetry. The network serves as the system of record for business communication. This puts Fusion in the position of being agnostic and able to provide a complete picture of what all the devices are doing, not just those that happen to have agents on them.
Collecting network telemetry in Fusion is a great way to ensure comprehensive visibility across your entire network and efficiently store months of history in a single place. The platform also provides hundreds of Network Detection Models (NDMs) that will fire an event when they see suspicious activity consistent with a network intrusion or security incident such as ransomware in your environment.
Of course, you have additional ways you might also detect an attack – through human detection, your EDR tool, or other layers for security. Whatever the means of detection, the next step is to piece together what happened. Fusion helps here, too.
Fusion’s investigation tools
In addition to network telemetry, Fusion has a set of tools that allows you to leverage network metadata to see the behavior of a potentially compromised host during a specific timeframe, including what else it talked to on your network. This helps you figure out the threat actor’s actions and gives you confidence that you have completely investigated the entire situation. Knowing the true scope of the incident is incredibly important for response and remediation.
You can access these tools in Fusion by going to the Investigate tab. Two commonly used tools are IP Intelligence and Traffic Top.
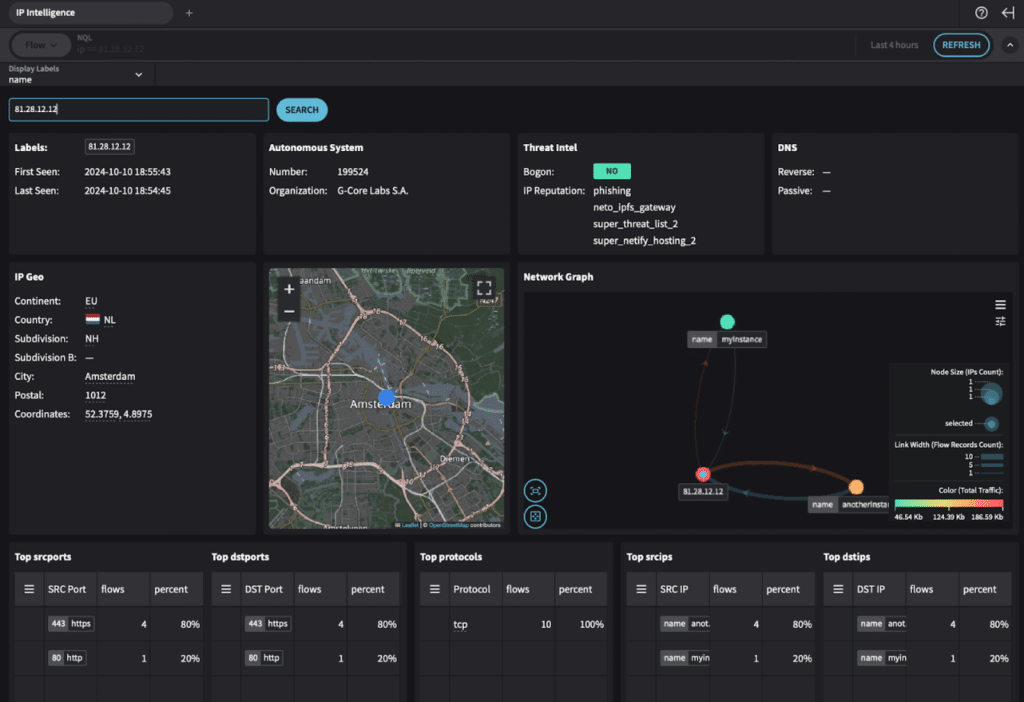
IP Intelligence provides a picture of interactions with external IP addresses during specific timeframes and additional information, such as their geolocations. You might learn about an IP address associated with incidents through a CISA bulletin or other intelligence sources. Simply enter that IP address and a timeframe, run a report, and see what sort of interaction your organization has had with that IP over that period. Or, say you know a user clicked on a phishing email and at approximately what time. You know the command and control (C2) IP address the attacker uses, so you can enter the C2 address into the tool to see the interactions that have happened since the email was opened.
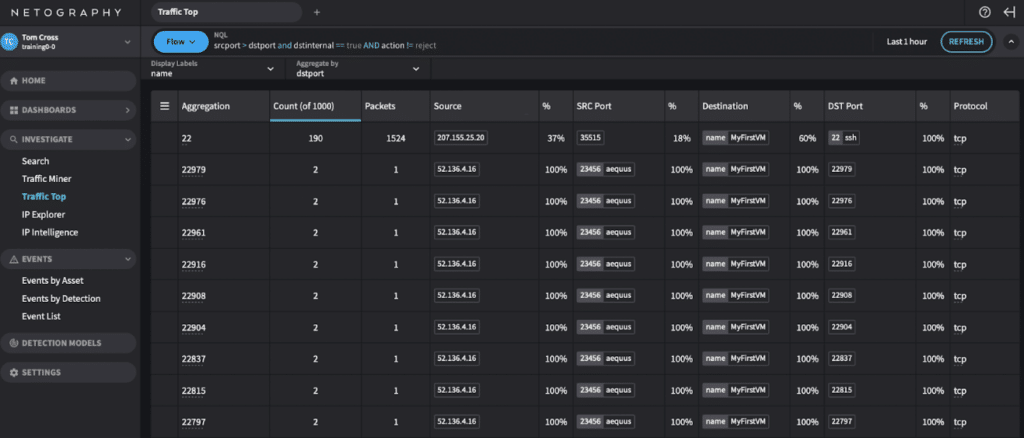
Traffic Top is another powerful investigation tool that aggregates network traffic search results by facets such as destination IP address or port. You can search for traffic coming from a particular source IP during a certain timeframe and see a list of the different destination IPs and ports that host communicated with. You can also narrow your searches in a variety of ways using Netography’s versatile search expression language, called NQL. This allows you to zero in on and quickly understand the behavior of hosts on your network. If a threat actor establishes a foothold in your network and they want to move laterally, this sort of metadata analysis can reveal scanning activities, lateral attacks, and other suspicious behaviors that merit further inspection.
This is just a sample of the activities you can search on and investigate with Fusion. The toolset also includes powerful tables and dashboards that show additional data in different views to help you quickly spot anomalous behavior.
It’s not a matter of if your organization’s network will be compromised but how well-prepared you are when that day comes. You need the ability to detect attacks your other defenses have missed and investigate activity within your network. Netography Fusion provides a history of metadata across your entire environment and a breadth of tools to inspect that data quickly, determine the scope, and accelerate a comprehensive response.