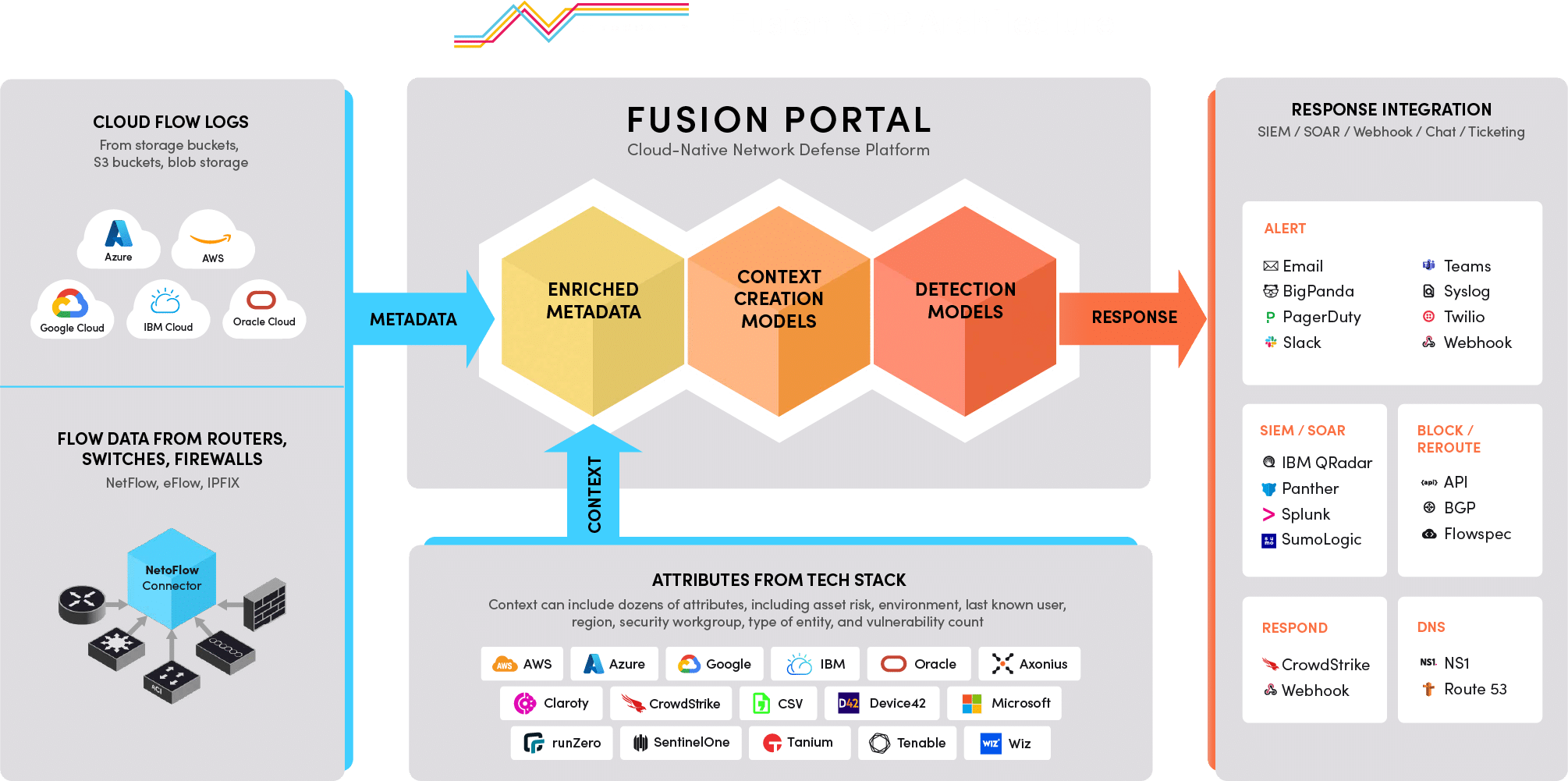
How Netography Fusion® Works
Cloud-Native Network Defense Platform for all Your Cloud and On-Prem Traffic
The Fusion platform gives you a unified view of all activity across your hybrid multi-cloud and on-prem network, including IT, OT, and IoT environments, without the need to deploy sensors, network taps, agents, or decryption architectures.
Your SecOps, SecDevOps, NetOps, and CloudOps teams will get time back in their day because Fusion reduces the time required to respond to any anomalies by delivering detailed, actionable alerts that include the context attributes of the devices involved in the activity. Your teams will understand the significance of the devices exhibiting the behavior without having to access additional tools.
By analyzing network activity at cloud scale, Netography Fusion provides critical insight for any organization struggling to gain fast, comprehensive knowledge of what your devices, users, applications, and data are doing.
“With this hybrid model of being cloud-native, being able to see that traffic and all those different lenses, both from an internal-to-external and also internal-to-internal perspective, is so important for us. Without having to deploy an appliance – I cannot underscore how important it is to call that out over and over. Time-to-value: when you’re able to get instant interpretations of data within minutes and see it on a graph, that’s just a beginning of increasing visibility.”

How It Works
Ingest
The 100% SaaS Netography Fusion platform starts with aggregating and normalizing metadata collected from your multi-cloud and on-prem network. The metadata consists of cloud flow logs from all five major cloud providers (Amazon Web Services, Microsoft Azure, Google Cloud, IBM Cloud, and Oracle Cloud) and flow data (NetFlow, sFlow, and IPFIX) from routers, switches, and other physical or virtual devices.
For those organizations that want to add an extra layer of security before sending their flow data to Fusion, they have the option of deploying NetoFlow Connector software that supports buffering, filtering, down sampling, and utilizes an HTTPS connection.
There are no additional components for you to install for Fusion to begin ingesting metadata from your existing tech stack. Its frictionless deployment model eliminates the additional cost and complexity of legacy appliance-based or agent-based approaches.
Enrich
Fusion then enriches this metadata with context contained in applications and services in your existing tech stack, including asset management, CMDB, EDR, NDR, XDR, and vulnerability management systems. The context can include dozens of attributes, including asset risk, environment, last known user, region, risk score, security workgroup, type of entity, and vulnerability count. Context transforms the metadata in your network from a table of IP addresses, ports, and protocols into context-rich descriptions of the activities of your users, applications, and devices. Enriched metadata accelerates your ability to detect compromise activity that other security controls in your stack have missed, such as anomalous lateral movement and data exfiltration.
Detect
Fusion detects anomalous and malicious activity with Netography Detection Models (NDMs). You have complete flexibility to customize Fusion’s preconfigured detection models as well as create your own models. Netography’s Detection Engineering team continuously create new NDMs as well as update existing models to detect new threats and variants of existing threats. For greater response effectiveness, multiple teams can utilize a single NDM to launch diverse response workflows, ensuring all teams have access to the same critical alerts.
Investigate
With Fusion’s tagging and context labeling, your teams can quickly visualize activity by application, location, compliance groups, or any other scheme. They can accelerate response time by quickly pivoting between dashboards to identify and investigate anomalous or malicious activity. They can also utilize the ability to “look back” to see up activity for up to 12 months prior, to understand the scope and duration of the activity.
Respond
The Fusion platform enables you to implement a range of response workflows quickly, including within the Fusion platform directly, or via built-in integrations with a range of technology partners, including EDR, NDR, and XDR systems, and SIEM/SOAR platforms. Well-documented RESTful APIs give you the ability to automate workflows with your tech stack as well, and Fusion also supports Terraform to enable you to automate the ability to provide visibility and control for scaling infrastructure.
Netography Query Language®
Netography Query Language® (NQL) is a powerful tool that enables analysts or operators to search enriched flow records by creating and saving custom algorithms.
You can create custom searches to rapidly analyze, investigate, and respond to anomalous or malicious traffic or incidents. You can also use these custom searches to create automated alerts and remediation workflows to meet your unique requirements.
With NQL you can isolate and analyze specific traffic, geo activity, threat actors, configurations, and more in seconds. It delivers the industry’s most granular and flexible flow record search capability, enabling you to create custom searches and alerts quickly and apply them to new or built-in dashboards.
NQL is the basis for accomplishing many tasks within Netography Fusion. Query examples include:
Becoming familiar with NQL will result in getting the most out of Netography Fusion. These generic rules apply regardless of where you leverage the query language:
- Logic must be unambiguous. e.g., A && B || C will fail. Use parens to prevent ambiguity.
- IP fields can be searched with CIDR notation if desired.
- 10.0.0.0/24 will match 10.0.0.1
- Only integer fields can use numerical comparisons. < <= > >=
- Strings with spaces must be quoted with single quotes.
- Allowed Boolean operators are: && AND and, || OR or, and !
- Allowed numerical operators are: == != < <= > >=
